Generate Ssh Public Key Mac Os X
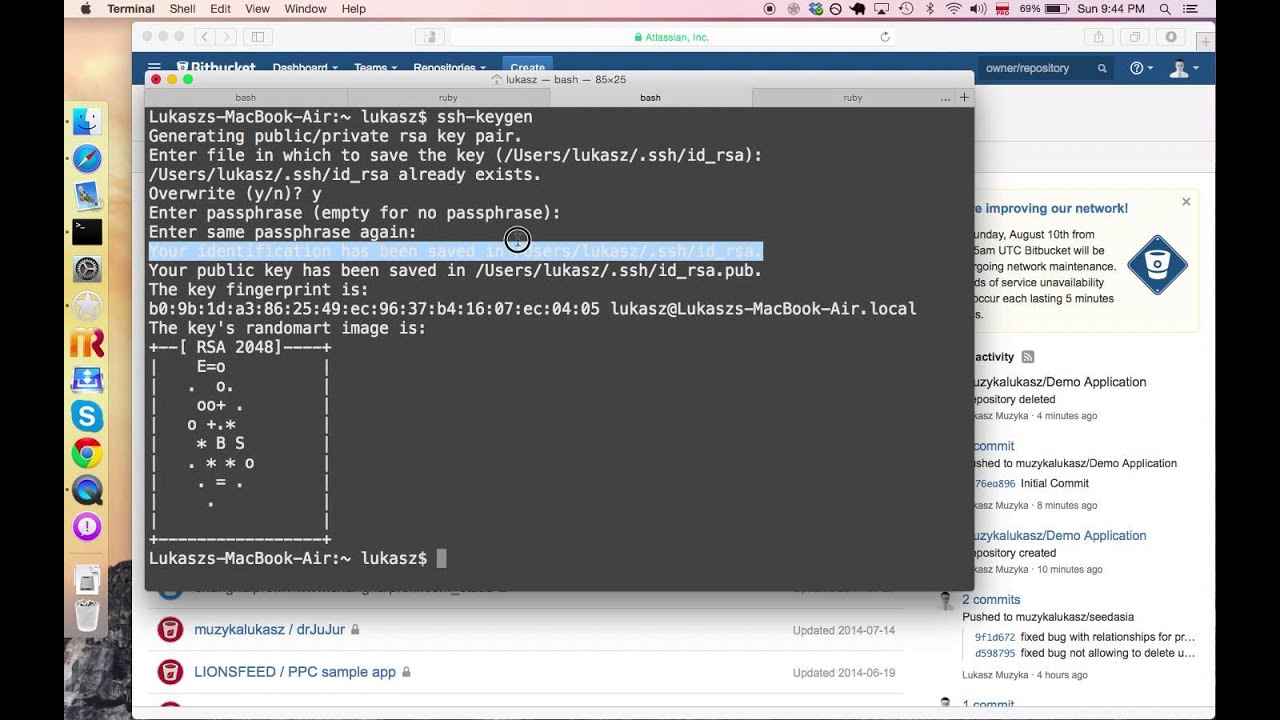
Mar 22, 2019 To generate a new Key pair, run the following commands on your home computer. Open your terminal and run the following command under your username. local$ ssh-keygen -t rsa This creates a public/private keypair of the type (-t) rsa.
 H
HUse the ssh-keygen command to generate SSH public and private key files. By default, these files are created in the /.ssh directory. You can specify a different location, and an optional password (passphrase) to access the private key file. If an SSH key pair with the same name exists in the given location, those files are overwritten. Creating an SSH key on Linux & macOS 1. Check for existing SSH keys. You should check for existing SSH keys on your local computer. You can use an existing SSH key with Bitbucket Server if you want, in which case you can go straight to either SSH user keys for personal use or SSH access keys for system use. Open a terminal and run the following. Run it on your local computer to generate a 2048-bit RSA key pair, which is fine for most uses. Ssh-keygen The utility prompts you to select a location for the keys. By default, the keys are stored in the /.ssh directory with the filenames idrsa for the private key and idrsa.pub for the public key. SSH and Tunneling. From OS X Scientific Computing. 4.1 Generate a public key on the computer you want to log in from. On Mac OS X, I use Safari as my primary. Oct 10, 2019 Encrypt/Decrypt a File using your SSH Public/Private Key on Mac OS X - idrsaencryption.md. Generate Your Private/Public Key-pair $ ssh-keygen -t rsa -C 'foo@example.com'. I've put together a script and usage instructions around this gist and with some tweaks to try to make it work across MacOS and Linux. Creating a SSH Public Key on OSX¶. You generate an SSH key through Mac OS X by using the Terminal application. Once you upload a valid public SSH key, Gerrit can authenticate you based on this key.
ow do I generate ssh keys under Linux / UNIX / Mac OS X and *BSD operating systems for remote login?SSH uses public-key cryptography to authenticate the remote computer and allow the remote computer to authenticate the user, if required. You can create ssh keys as follows on any Linux or UNIX-like operating systems including Mac OS X.[donotprint][/donotprint]
Generate Ssh Public Key Mac Os X 10 12
ssh-keygen command to Generate SSH Keys
The ssh-keygen command generates, manages and converts authentication keys for ssh client and server usage. Type the following command to generate ssh keys (open terminal and type the command):$ ssh-keygen
Generate SSH keys looks as follows:
Ssh Public Key Authentication
The above command creates ~/.ssh/ directory. So if your user name is vivek, than all files are stored in /home/vivek/.ssh/ or $HOME/.ssh/ directory as follows:
- $HOME/.ssh/id_rsa – Your private key. Do not share this file with anyone. Keep it private
- $HOME/.ssh/id_rsa.pub– Your public key.
Please note that the passphrase must be different from your current password and do not share keys or passphrase with anyone. Also, make sure you have correct and secure permissions on $HOME/.ssh/ directory:
All Activation keys of Softwares and WIndows. Cubase Pro 9.5.40 Crack + Serial Key Free Download Full Version Cubase Pro 9.5.40 Crack is providing Groundbreaking new features, streamlined workflows, and incredible brand. Mar 29, 2014 I recently recieved a pre-owned copy of Sid Meier's Civilization V as a gift. I was so exited, that I logged into Steam, and began to install it immediately. However, due to the fact that it is pre-owned, the product activation code was invalid. Is there any way that I can get past this issue? May 10, 2016 Sid meiers civilization v cd key Sid meiers civilization v serial key Sid mei. Aug 02, 2015 We are extremely happy that we can share it with you. We worked on this Civilization V CD Key Hack really hard, so in return we expect you to appreciate our work.All that you need to do to get some free cd keys is to download our tool “Civilization V Key Generator” and run it. Civilization v product key generator free.
SSH Keys Are Generated, What Next?
You need to copy $HOME/.ssh/id_rsa.pub file to remote server so that you can login using keys instead of the password. Google api key generator online. Use any one of the following command to copy key to remote server called vpn22.nixcraft.net.in for vivek user:ssh-copy-id vivek@vpn22.nixcraft.net.in
On some *nix system such as OS X ssh-copy-id command may not be installed, use the following commands (when prompted provide the password for remote user account called vivek) to install/append the public key on remote host:ssh vivek@vpn22.nixcraft.net.in 'umask 077; mkdir .ssh'
cat $HOME/.ssh/id_rsa.pub ssh vivek@vpn22.nixcraft.net.in 'cat >> .ssh/authorized_keys'
To login simply type:ssh vivek@vpn22.nixcraft.net.in
The following command will help to remember passphraseexec ssh-agent $SHELL
ssh-add
ssh vivek@vpn22.nixcraft.net.in
Optional ssh-keygen command syntax for advance users
The following syntax specifies the 4096 of bits in the RSA key to creation (default 2048):ssh-keygen -t rsa -b 4096 -f ~/.ssh/aws.key -C 'My AWs cloud key'
Where,
- -t rsa : Specifies the type of key to create. The possible values are “rsa1” for protocol version 1 and “dsa”, “ecdsa”, “ed25519”, or “rsa” for protocol version 2.
- -b 4096 : Specifies the number of bits in the key to create.
- -f ~/.ssh/aws.key : Specifies the filename of the key file.
- -C 'My AWs cloud key' : Set a new comment.
Now install the ~/.ssh/aws.key, run:ssh-copy-id -i ~/.ssh/aws.key user@aws-server-ip
Test it with the ssh command:ssh -i ~/.ssh/aws.key ec2-user@aws-server-ip
See “How To Set up SSH Keys on a Linux / Unix System” for more info.
Conclusion
You learned how to create and generate ssh keys using the ssh-keygen command.
- Howto Linux / UNIX setup SSH with DSA public key authentication (password less login)
- sshpass: Login To SSH Server / Provide SSH Password Using A Shell Script
- keychain: Set Up Secure Passwordless SSH Access For Backup Scripts
- Openssh man pages here
- Man pages – ssh-keygen(1)
ADVERTISEMENTS
This guide will demonstrate the steps required to encrypt and decrypt files using OpenSSL on Mac OS X. The working assumption is that by demonstrating how to encrypt a file with your own public key, you'll also be able to encrypt a file you plan to send to somebody else using their private key, though you may wish to use this approach to keep archived data safe from prying eyes.
Too Long, Didn't Read
Assuming you've already done the setup described later in this document, that id_rsa.pub.pcks8 is the public key you want to use, that id_rsa is the private key the recipient will use, and secret.txt is the data you want to transmit…
Encrypting
Decrypting
Using Passwords
OpenSSL makes it easy to encrypt/decrypt files using a passphrase. Unfortunately, pass phrases are usually 'terrible' and difficult to manage and distribute securely.
To Encrypt a File
You can add -base64 if you expect the context of the text may be subject to being 'visible' to people (e.g., you're printing the message on a pbulic forum). If you do, you'll need to add it to the decoding step as well. You can choose from several cypers but aes-256-cbc is reasonably fast, strong, and widely supported. Base64 will increase the size of the encrypted file by approximately 30%
To Decrypt a File
You will need to provide the same password used to encrypt the file. All that changes between the encrypt and decrypt phases is the input/output file and the addition of the -d flag. If you pass an incorrect password or cypher then an error will be displayed.
Encrypting Files Using your RSA keys
RSA encryption can only work with very short sections of data (e.g. an SHA1 hash of a file, or a password) and cannot be used to encrypt a large file. The solution is to generate a strong random password, use that password to encrypt the file with AES-256 in CBC mode (as above), then encrypt that password with a public RSA key. The encrypted password will only decrypt with a matching public key, and the encrypted file will require the unique password encrypted in the by the RSA key.
Replace OpenSSL
The copy of OpenSSL bundled with Mac OS X has several issues. Mac OS X 10.7 and earlier are not PCI compliant. It is best to replace it. See here for details: http://www.dctrwatson.com/2013/07/how-to-update-openssh-on-mac-os-x/
Generate Your Private/Public Key-pair
By default your private key will be stored in
- ~/.ssh/id_rsa : This is your private key and it must be kept secret
- ~/.ssh/id_rsa.pub : This is your public key, you can share it (for example) with servers as an authorized key for your account.You can change the location of where you store your keys, but this location is typical. Typically you want to ensure the private key is chmod 600, andd the public key is chmod 644.
Generate a PKCS8 Version of Your Public Key
The default format of id_rsa.pub isn't particularly friendly. If you are going to public your key (for example) on your website so that other people can verify the authorship of files attributed to you then you'll want to distribute it in another format. I find it useful to keep a copy in my .ssh folder so I don't have to re-generate it, but you can store it anywhere you like.
Generate a One-Time-Use Password to Encrypt the File
The passwords used to encrypt files should be reasonably long 32+ characters, random, and never used twice. To do this we'll generate a random password which we will use to encrypt the file.
This will generate 192 bytes of random data which we will use as a key. If you think a person may need to view the contents of the key (e.g., they're going to display it on a terminal or copy/paste it between computers) then you should consider base-64 encoding it, however:
- The password will become approximately 30% longer (and there is a limit to the length of data we can RSA-encrypt using your public key
- The password will be 'padded' with '=' characters if it's not a multiple of 4 bytes.
A Note on Long Passwords
There is a limit to the maximum length of a message that can be encrypted using RSA public key encryption. If you want to use very long keys then you'll have to split it into several short messages, encrypt them independently, and then concatinate them into a single long string. Decrypting the password will require reversing the technique: splitting the file into smaller chuncks, decrypting them independently, and then concatinating those into the original password key file.
Encrypt the File Using the Generated Key
Now that you have a good random password, you can use that to AES encrypt a file as seen in the 'with passwords' section
Decrypting the file works the same way as the 'with passwords' section, except you'll have to pass the key.
Encrypt the Key Used to Encrypt the File
We used fast symetric encryption with a very strong password to encrypt the file to avoid limitations in how we can use asymetric encryption. Finally, we'll use asymetric encryption to encrypt the password. This solves the problem of 'how do I safely transmit the password for the encrypted file' problem. You can encrypt is using the recipients public key and they can decode it using their private key. Encrypt the password using a public key:
The recipient can decode the password using a matching private key:
Package the Encrypted File and Key
There are a number of ways to do this step, but typically you'll want just a single file you can send to the recipent to make transfer less of a pain. I'd recommend just making a tarball and delivering it through normal methods (email, sftp, dropbox, whatever). Though a secure method of exchange is obviously preferable, if you have to make the data public it should still be resistent to attempts to recover the information.
The file can be extracted in the usual way:
Generate Ssh Key On Mac
You may want to securely delete the unecrypted keyfile as the recipient will be able to decode it using their private key and you already have the unencrypted data.