Ssh Key Generate Windows Cmd
- Generate Ssh Key Windows Cmder
- Ssh Key Generate Windows Cmd Download
- Ssh Key Generate Windows Cmd Password
Updated by LinodeWritten by Linode
Sep 26, 2019 Generating an SSH key manually. Modified: 26 Sep 2019 21:20 UTC. Use these instructions to manually generate and upload an SSH key to the Triton Compute Service portal. This section shows you how to manually generate and upload. Creating an SSH key on Windows 1. Check for existing SSH keys. You should check for existing SSH keys on your local computer. You can use an existing SSH key with Bitbucket Server if you want, in which case you can go straight to either SSH user keys for personal use or SSH access keys for system use. Open a command prompt, and run. Just download and install openSSH for windows. It is open source, and it makes your cmd ssh ready. A quick google search will give you a tutorial on how to install it, should you need it. After it is installed you can just go ahead and generate your public key if you want to put in on a server. You generate it by running: ssh-keygen -t rsa.
Report an Issue View File Edit File
Password authentication is the default method most SSH (Secure Shell) clients use to authenticate with remote servers, but it suffers from potential security vulnerabilities, like brute-force login attempts. An alternative to password authentication is public key authentication, in which you generate and store on your computer a pair of cryptographic keys and then configure your server to recognize and accept your keys. Using key-based authentication offers a range of benefits:
Key-based login is not a major target for brute-force hacking attacks.
If a server that uses SSH keys is compromised by a hacker, no authorization credentials are at risk of being exposed.
Because a password isn’t required at login, you are able to able to log in to servers from within scripts or automation tools that you need to run unattended. For example, you can set up periodic updates for your servers with a configuration management tool like Ansible, and you can run those updates without having to be physically present.
This guide will explain how the SSH key login scheme works, how to generate an SSH key, and how to use those keys with your Linode.
NoteHow SSH Keys Work
SSH keys are generated in pairs and stored in plain-text files. The key pair (or keypair) consists of two parts:
A private key, usually named
id_rsa. The private key is stored on your local computer and should be kept secure, with permissions set so that no other users on your computer can read the file.Caution
A public key, usually named
id_rsa.pub. The public key is placed on the server you intend to log in to. You can freely share your public key with others. If someone else adds your public key to their server, you will be able to log in to that server.
When a site or service asks for your SSH key, they are referring to your SSH public key (id_rsa.pub). For instance, services like GitHub and Gitlab allow you to place your SSH public key on their servers to streamline the process of pushing code changes to remote repositories.
The authorized_keys File
In order for your Linode to recognize and accept your key pair, you will need to upload your public key to your server. More specifically, you will need to upload your public key to the home directory of the user you would like to log in as. If you would like to log in to more than one user on the server using your key pair, you will need to add your public key to each of those users.
To set up SSH key authentication for one of your server’s users, add your public key to a new line inside the user’s authorized_keys file. This file is stored inside a directory named .ssh/ under the user’s home folder. A user’s authorized_keys file can store more than one public key, and each public key is listed on its own line. If your file contains more than one public key, then the owner of each key listed will be able to log in as that user.
Granting Someone Else Access to your Server
To give someone else access to your server’s user, simply add their public key on a new line in your authorized_keys file, just as you would add your own. To revoke access for that person, remove that same line and save the changes.
Challenge-Response
When logging in to a server using SSH, if there is a public key on file on that server, the server will create a challenge. This challenge will be crafted in such a way that only the holder of the private SSH key will be able to decipher it.
This challenge-response action happens without any user interaction. If the person attempting to log in has the corresponding private key, then they will be safely logged in. If not, the login will either fail or fall back to a password-based authentication scheme.
SSH Key Passphrases
You can optionally provide an additional level of security for your SSH keys by encrypting them with a passphrase at the time of creation. When you attempt to log in using an encrypted SSH key, you will be prompted to enter its passphrase. This is not to be confused with a password, as this passphrase only decrypts the key file locally and is not transferred over the Internet as a password might be.
If you’d like to set up your logins so that they require no user input, then creating a passphrase might not be desirable, but it is strongly recommended nevertheless.
Linux and macOS
Generate a Key Pair
Perform the steps in this section on your local machine.
Create a new key pair.
Caution
This command will overwrite an existing RSA key pair, potentially locking you out of other systems.
If you’ve already created a key pair, skip this step. To check for existing keys, run
ls ~/.ssh/id_rsa*.If you accidentally lock yourself out of the SSH service on your Linode, you can still use the Lish console to login to your server. After you’ve logged in via Lish, update your
authorized_keysfile to use your new public key. This should re-establish normal SSH access.The
-bflag instructsssh-keygento increase the number of bits used to generate the key pair, and is suggested for additional security.Press Enter to use the default names
id_rsaandid_rsa.pubin the/home/your_username/.sshdirectory before entering your passphrase.While creating the key pair, you will be given the option to encrypt the private key with a passphrase. This means that the key pair cannot be used without entering the passphrase (unless you save that passphrase to your local machine’s keychain manager). We suggest that you use the key pair with a passphrase, but you can leave this field blank if you don’t want to use one.
Upload your Public Key
There are a few different ways to upload your public key to your Linode from Linux and macOS client systems:
Using ssh-copy-id
ssh-copy-id is a utility available on some operating systems that can copy a SSH public key to a remote server over SSH.
To use
ssh-copy-id, pass your username and the IP address of the server you would like to access:You’ll see output like the following, and a prompt to enter your user’s password:
Verify that you can log in to the server with your key.
Using Secure Copy (scp)
Secure Copy (scp) is a tool that copies files from a local computer to a remote server over SSH:
authorized_keys file on your server. If you have already set up other public keys on your server, use the ssh-copy-id command or enter your key manually.Connect to your server via SSH with the user you would like to add your key to:
Create the
~/.sshdirectory andauthorized_keysfile if they don’t already exist:Give the
~/.sshdirectory andauthorized_keysfiles appropriate file permissions:In another terminal on your local machine, use
scpto copy the contents of your SSH public key (id_rsa.pub) into theauthorized_keysfile on your server. Substitute in your own username and your server’s IP address:Verify that you can log in to the server with your key.
Manually Copy an SSH Key
You can also manually add an SSH key to a server:
Begin by copying the contents of your public SSH key on your local computer. You can use the following command to output the contents of the file:
You should see output similar to the following:
Note that the public key begins with
ssh-rsaand ends with[email protected].Once you have copied that text, connect to your server via SSH with the user you would like to add your key to:
Create the
~/.sshdirectory andauthorized_keysfile if they don’t already exist:Give the
~/.sshdirectory andauthorized_keysfiles appropriate file permissions:Open the
authorized_keysfile with the text editor of your choice (nano, for example). Then, paste the contents of your public key that you copied in step one on a new line at the end of the file.Save and close the file.
Note
If you initially logged into the server as
rootbut edited theauthorized_keysfile of another user, then the.ssh/folder andauthorized_keysfile of that user may be owned byroot. Set that other user as the files’ owner:Verify that you can log in to the server with your key.
Connect to the Remote Server
SSH into the server from your local machine:
If you chose to use a passphrase when creating your SSH key, you will be prompted to enter it when you attempt to log in. Depending on your desktop environment, a window may appear:
Caution
Do not allow the local machine to remember the passphrase in its keychain unless you are on a private computer which you trust.You may also see the passphrase prompt at your command line:
Enter your password. You should see the connection establish in the local terminal.
Windows
The following instructions use the PuTTY software to connect over SSH, but other options are available on Windows too.
Generate a Key Pair with PuTTY
Download PuTTYgen (
puttygen.exe) and PuTTY (putty.exe) from the official site.Launch
puttygen.exe. TheRSAkey type at the bottom of the window is selected by default for an RSA key pair butED25519(EdDSA using Curve25519) is a comparable option if your remote machine’s SSH server supports DSA signatures. Do not use theSSH-1(RSA)key type unless you know what you’re doing.Increase the RSA key size from
2048bits4096and click Generate:PuTTY uses the random input from your mouse to generate a unique key. Once key generation begins, keep moving your mouse until the progress bar is filled:
When finished, PuTTY will display the new public key. Right-click on it and select Select All, then copy the public key into a Notepad file.
Save the public key as a
.txtfile or some other plaintext format. This is important–a rich text format such as.rtfor.doccan add extra formatting characters and then your private key won’t work:Enter a passphrase for the private key in the Key passphrase and Confirm passphrase text fields. Important: Make a note of your passphrase, you’ll need it later:
Click Save private key. Choose a file name and location in Explorer while keeping the
ppkfile extension. If you plan to create multiple key pairs for different servers, be sure to give them different names so that you don’t overwrite old keys with new:
Manually Copy the SSH Key with PuTTY
Launch
putty.exe. Find the Connection tree in the Category window, expand SSH and select Auth. Click Browse and navigate to the private key you created above:Scroll back to the top of the Category window and click Session. Enter the hostname or IP address of your Linode. PuTTY’s default TCP port is
22, the IANA assigned port for for SSH traffic. Change it if your server is listening on a different port. Name the session in the Saved Sessions text bar and click Save:Click the Open button to establish a connection. You will be prompted to enter a login name and password for the remote server.
Once you’re logged in to the remote server, configure it to authenticate with your SSH key pair instead of a user’s password. Create an
.sshdirectory in your home directory on your Linode, create a blankauthorized_keysfile inside, and set their access permissions:Open the
authorized_keysfile with the text editor of your choice (nano, for example). Then, paste the contents of your public key that you copied in step one on a new line at the end of the file.Save, close the file, and exit PuTTY.
Verify that you can log in to the server with your key.
Using WinSCP
Uploading a public key from Windows can also be done using WinSCP:
Cautionauthorized_keys file on your server. If you have already set up other public keys on your server, use the PuTTY instructions instead.In the login window, enter your Linode’s public IP address as the hostname, the user you would like to add your key to, and your user’s password. Click Login to connect.
Once connected, WinSCP will show two file tree sections. The left shows files on your local computer and the right shows files on your Linode. Using the file explorer on the left, navigate to the file where you saved your public key in Windows. Select the public key file and click Upload in the toolbar above.
You’ll be prompted to enter a path on your Linode where you want to upload the file. Upload the file to
/home/your_username/.ssh/authorized_keys.Verify that you can log in to the server with your key.
Connect to the Remote Server with PuTTY
Start PuTTY and Load your saved session. You’ll be prompted to enter your server user’s login name as before. However, this time you will be prompted for your private SSH key’s passphrase rather than the password for your server’s user. Enter the passphrase and press Enter.
Troubleshooting
If your SSH connections are not working as expected, or if you have locked yourself out of your system, review the Troubleshooting SSH guide for troubleshooting help.
Upload your SSH Key to the Cloud Manager
It is possible to provision each new Linode you create with an SSH public key automatically through the Cloud Manager.
Log in to the Cloud Manager.
Click on your username at the top right hand side of the page. Then click on My Profile in the dropdown menu that appears:
Note
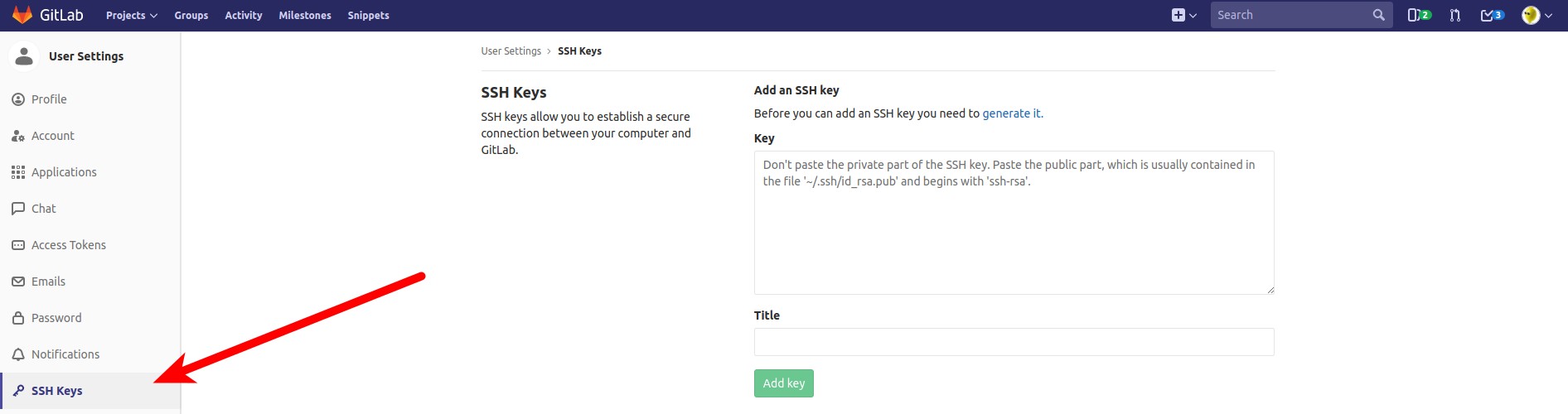
If you are viewing the Cloud Manager in a smaller browser window or on a smaller device, then the My Profile link will appear in the sidebar links. To view the sidebar links, click on the disclosure button to the left of the blue Create button at the top of the page.From the My Profile page, select the SSH Keys tab, and then click Add a SSH Key:
Create a label for your key, then paste in the contents of your public SSH key (
id_rsa.pub):Click Add Key.
When you next create a Linode you’ll be given the opportunity to include your SSH key in the Linode’s creation. This key will be added to the root user of the new Linode.
In the Create Linode form, select the SSH key you’d like to include. This field will appear below the Root Password field:
Next Steps
After you set up your SSH keys and confirm they are working as expected, review the How to Secure Your Server guide for instructions on disabling password authentication for your server.
Join our Community
This guide is published under a CC BY-ND 4.0 license.
PuTTYgen is a key generator tool for creating pairs of public and private SSH keys. It is one of the components of the open-source networking client PuTTY. Although originally written for Microsoft Windows operating system, it is now officially available for multiple operating systems including macOS, Linux. PuTTYgen.exe is the graphical tool on Windows OS. While on the other side, Linux OS has the only command-line version could be accessible using SSH commands.
Generate Ssh Key Windows Cmder
- 1 Download PuTTYgen
- 1.1 Download PuTTYgen on Windows
- 1.2 Download PuTTYgen for Mac
- 1.3 Download PuTTYgen for Ubuntu/Linux
- 1.3.3 Types of Keys Supported on PuTTYgen
Puttygen aka Putty Key Generator
The key generation utility – PuTTYgen can create various public-key cryptosystems including Rivest–Shamir–Adleman (RSA), Digital Signature Algorithm (DSA), Elliptic Curve Digital Signature Algorithm (ECDSA), and Edwards-curve Digital Signature Algorithm (EdDSA) keys.
The aforementioned public-key cryptosystems principally focus on secure data transmission and digital signatures.
Although PuTTYgen collects keys in its native file format i.e. .ppk files, the keys can easily be converted to any file format. For Windows, the software interface is PuTTYgen.exe, whereas, for Linux OS the command-line adaptation is available using SSH commands.
How to use PuTTYgen?
PuTTYgen is used to generate public or private key pair for creating SSH keys. Below is the complete guidance about how to generate RSA key in the Windows operating system:
- Once you install the PuTTY on your machine, you can easily run PuTTYgen. For the same, go to Windows -> Start Menu -> All Programs -> PuTTY -> PuTTYgen.
- You will see the PuTTY key generator dialog box on your screen
- You will find a “Generate” button in that dialog. Clicking on it will lead to generating the keys for you.
- Now you will need to add a unique key passphrase in the Key passphrase and Confirm passphrase field.
- Click on the “Save Public Key” and “Save Private Key” buttons to save your public and private keys.
- You will see the text starting with ssh-RSA in the Public key for pasting into OpenSSH authorized_keys file field which is located at the top of the window. Copy that entire text to your clipboard by pressing ctrl+c as you will require the key to paste on your clipboard in the public key tool of control panel or directly on the cloud server.
Various Ways to Use RSA Key Pair
RSA key pair generated through PuTTYgen is used in two various ways defined as below:
- To assign while creating a new cloud server
You can choose the public key from the given list of keys at the time of creating a cloud server. If you don’t find your key in that list, then first add and then assign it. - Assign to an existing cloud server
At the time of connecting to the cloud server, first of all, you need to tell PuTTY to use it for utilizing your newly created RSA key pair.
PuTTYgen being a component of the terminal emulator PuTTY does not have to be downloaded separately, hence, comes with the PuTTY .msi installation package. You can follow the simple steps to download PuTTYgen software for your system. That is the reason why you don’t need to download PuTTYgen separately. Once you download PuTTY software, you will be able to install and run PuTTYgen easily in no time. Below is the complete instruction about how to download and install PuTTY on Windows.
Apart from that, it is also integrated into third-party programs such as WinSCP installation package. Below you can find a complete PuTTYgen download and installation guide for all operating systems.
Download PuTTYgen on Windows
To download PuTTYgen the primary requisite is to acquire the copy of PuTTY installation package. For the 64-bit operating system, one must install the 64-bit version of PuTTY, i.e. putty-64bit-<version>-installer.msi.Similarly, for the 32-bit operating system, the respective 32-bit version of PuTTY, i.e. putty-<version>-installer.msi needs to be installed.
To get PuTTY, go to PuTTY Installation Download page, whereby the complete installation package will be available with setup instructions, installation guide, and download links to all other components of PuTTY such as putty.exe, pscp.exe, psftp.exe, puttytel.exe, plink.exe, pageant.exe and putty.zip.
Following the successful download of the PuTTY installation package. It is time to install the program. Go to How to install PuTTY on Windows, whereby you will find the step by step guidance for PuTTY installation for Windows operating system.
After successfully downloading and installing PuTTY on your Windows machine, you are just 2-3 clicks away to run PuTTYgen. Follow the below-given step by step guidance to run PuTTYgen:
Run PuTTYgen on Windows
To run PuTTYgen, Go to Windows -> Start Menu -> All Programs -> PuTTY -> PuTTYgen. You will see a window for the PuTTY Key Generator on your screen.
Voila! Now you can generate public or private key pair using PuTTYgen.
Download PuTTYgen for Mac
Below is the detailed guide to download PuTTYgen on Mac operating system. Mac OS has a built-in command-line SSH client known as Terminal. To utilize it, go to Finder and then opt for Go -> utilities from the top menu. After that find the terminal which supports SSH connections to remote servers.
However, to run PuTTYgen for mac, the first one must have to install PuTTY. There are multiple ways to install PuTTY, which are Homebrew or MacPorts. Both alternatives will also install the command-line of adaptations of PuTTYgen.
Ported PuTTY for Mac
Mac has the port of PuTTY which can be installed in various ways described as below:
- Installation using Homebrew:
First, install the ‘brew command line’ Once installed use the below-given command to install PuTTY:-sudo brew install putty - Installation using MacPorts:
First of all, one must install MacPorts and then use the command-line to install PuTTY. Here is the command to install PuTTY via MacPortssudo port install putty
Additionally, a user can also add a shortcut to the desktop by writing the following command line–cp /opt/local/bin/putty ~/Desktop/PuTTY
However, there is an alternative way to install PuTTY on Mac OS. Cyberduck is a widely used Mac OS SSH Client. Once PuTTY installed on the Mac OS, a user can convert PuTTY derived private key format to OpenSSH.
To convert the private key to standard PEM format, type the following command –
puttygen privatekey.ppk -O private-openssh -o privatekey.pem
You can also read the guide to convert .pem file to .ppk using puttygen.
Download PuTTYgen for Ubuntu/Linux
To download PuTTYgen for Ubuntu (Linux) operating system, a user to first install PuTTY. However, in some Linux distributions, the SSH key generation tool – PuTTYgen needs to be installed independently from the PuTTY client.
For example, Debian Linux requires the below-given code to install PuTTYgen:
sudo apt install putty-tools
Generate Key Pair for Authentication in Linux
To create the key pair for authentication in Linux use the below command:-
puttygen -t rsa -b 2048 -C 'user@host' -o keyfile.ppk
Various Command Line Options of PuTTY in Linux
Below are few important command line options in the Linux operating system for PuTTY:

PuTTYgen [-t keytype [-b bits] [-q] keyfile]
[-C new-comment] [-P]
[-O output-type -p -l -L]
[-o output-file]
Options:
Ssh Key Generate Windows Cmd Download
- Keyfile – It is the name of the existing key file to read at the time of changing the current key.
- –t keytype – The command specifies the type of key to creating. Its acceptable values are RSA and dsa.rsa1.
- -b bits – This command specifies a total number of bit in a particular key. 1024 is the perfect size for DSA key, while 2048 or 4096 are the perfect size for RSA keys.
- –q – The command suppresses the message about progress at the time of key generation.
- -C new-comment – The command will specify the comment to describe the key. It can be used for the new and/or existing key. Key operation is not affected by a comment. However, it is used to recognize the key owner, it’s not reliable completely as any value can be applied to it.
- –P – Using the command will update the passphrase of a key. Passphrase helps to encrypt the private key. As passphrase can’t add or update on a command line, it prompts a new passphrase tool to alter it.
- –old-passphrase-file – The old password of the key remains in this file. The command is used when the key is protected by a passphrase.
- –new-passphrase file – This command prompts the new passphrase of the key. It comes in the action either at the time of generating a new key or while applying –P command to change the passphrase.
- -O output-type – This command defines what to give in output. By default, the private key is the output.
Thus, above are the prominent commands of PuTTYgen in Linux operating system. Besides that, there are many other commands available to perform various tasks from the command prompt in Linux at flank speed.
Types of Keys Supported on PuTTYgen
Ssh Key Generate Windows Cmd Password
It is important to know the types of key PuTTYgen supports prior to using it. Below are the key types that it currently supports for SSH-2 and SSH-1 protocol:-
- SSH-1 protocol:- For SSH-1 only supports one key i.e. Rivest–Shamir–Adleman (RSA)
- SSH-2 protocol: – SSH-2 supports multiple key types that include – Digital Signature Algorithm (DSA), Elliptic Curve Digital Signature Algorithm (ECDSA) and Ed25519.
The above description is a detailed brief on downloading and running PuTTYgen on all major operating systems. For further details please check the Download PuTTY page.
Traffic Encryption Key (TEK) KEY. A traffic encryption key (TEK) enables the SINCGARS radio to operate. In a secure, cipher text (CT) mode of communications. Loaded into the SINCGARS RT from an ANCD, or other COMSEC fill. Device, if desired. A TEK may be loaded into all six channels of the RT, or channel 6 may be. Public key encryption.