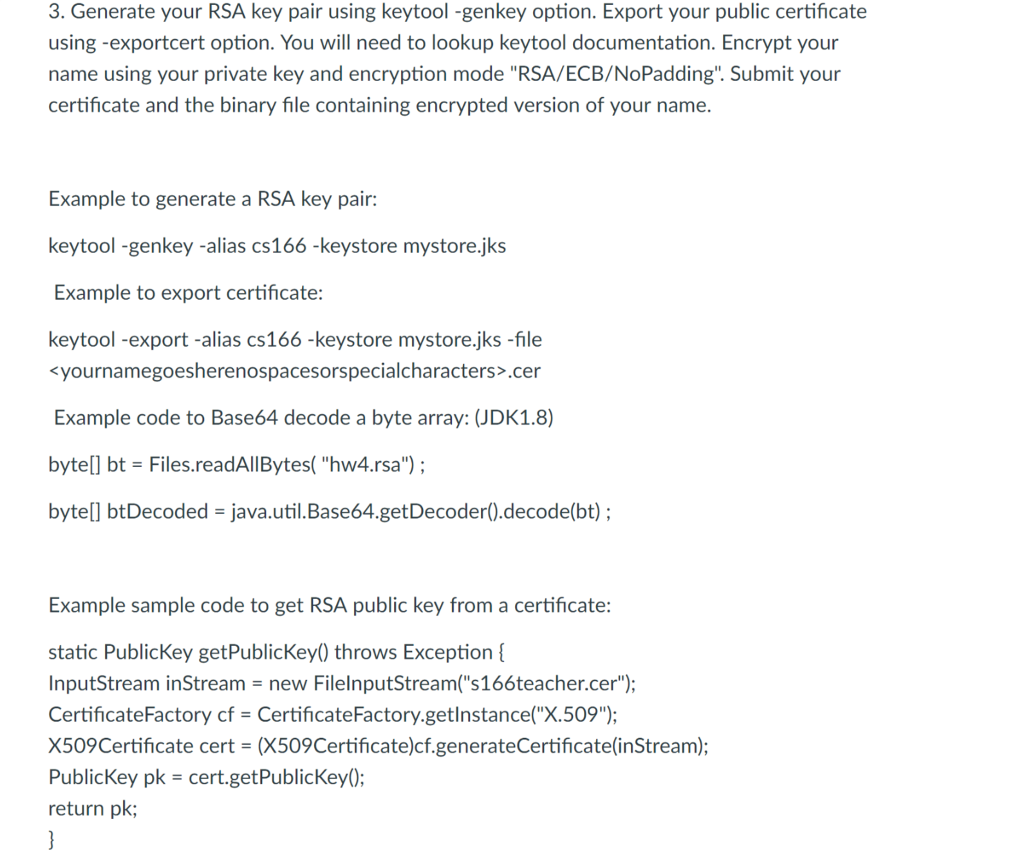
Java Read Public Key Generate Private Key
- Java Read Public Key Generate Private Key From Bitcoin Address
- Java Key Events
- Java Read Public Key Generate Private Keys
- Java Read Public Key Generate Private Key In Ec2 Aws
Oct 29, 2019 Parse RSA public and private key pair from string in Java - ParseRSAKeys.java. Parse RSA public and private key pair from string in Java - ParseRSAKeys.java. Skip to content. All gists Back to GitHub. Sign in Sign up. Openssl rsa -pubout -in privatekey.pem -out publickey.pem. Press generate and follow instructions to generate (public/private) key pair. Create a new 'authorizedkeys' file (with Notepad): Copy your public key data from the 'Public key for pasting into OpenSSH authorizedkeys file' section of the PuTTY Key Generator, and paste the key data to the 'authorizedkeys' file. Generating a Secure Shell (SSH) Public/Private Key Pair Several tools exist to generate SSH public/private key pairs. The following sections show how to generate an SSH key pair on UNIX, UNIX-like and Windows platforms. Generate a private-public key pair using keytool. Save/Load Private and Public Key to/from a file. Store/Retrieve Private Key/Public Key to. The most popular Public Key Algorithms are RSA, Diffie-Hellman, ElGamal, DSS. Generate a Public-Private Key Pair. There are several ways to generate a Public-Private Key Pair depending on your platform. In this example, we will create a pair using Java. The Cryptographic Algorithm we will use in this example is RSA.
Mar 29, 2016 This tutorial explains how to create a public private keystore for client and server. You can use these keystores to secure communication between client and server. Following steps are required for generating a public private keystore.
Java Read Public Key Generate Private Key From Bitcoin Address
Public Keys, Private Keys, and Certificates
When performing authentication, SSL uses a technique called public-key cryptography.
Public-key cryptography is based on the concept of a key pair,which consists of a public key and a privatekey. Data that has been encrypted with a public key canbe decrypted only with the corresponding private key. Conversely,data that has been encrypted with a private key can be decrypted onlywith the corresponding public key.
The owner of the key pair makes the public key available toanyone, but keeps the private key secret.
A certificate verifies that anentity is the owner of a particular public key.
Therefore, Its latest Version Has lots of latest Features Like Photo Editor, Disc Burn. Also, it allows you to create bootable ISO images as well as write a bootable image to a flash drive. Daemon tools 5.0.1 key code generator download. It will enable various mounting types of image files and lets you create dozens of virtual disks.DAEMON Tools Pro 8 Crack is a User-Friendly Interface and straightforward to use program.
Certificatesthat follow the X.509 standard contain a data section and a signaturesection. The data section includes such information as:
The Distinguished Name of the entity that owns thepublic key
The Distinguished Name of the entity that issued thecertificate
The period of time during which the certificate isvalid
The public key itself
You can obtain a certificate from a Certificate Authority(CA) such as VeriSign. Alternately, you can createa self-signed certificate, in which the ownerand the issuer are the same.
An organization that issues certificates can establish a hierarchyof CAs. The root CA has a self-signed certificate. Each subordinateCA has a certificate that is signed by the next highest CA in thehierarchy. A certificate chain isthe certificate of a particular CA, plus the certificates of any higherCAs up through the root CA.
- Related Questions & Answers
- Selected Reading
Private Keys and Public Keys terms are used in encryption and decryption. These keys are used to encrypt/decrypt sensitive information.
Private Key
The private key is used to both encrypt and decrypt the data. This key is shared between the sender and receiver of the encrypted sensitive information. The private key is also called symmetric being common for both parties. Private key cryptography is faster than public-key cryptography mechanism.
Public Key
Java Key Events
The public key is used to encrypt and a private key is used decrypt the data. The private key is shared between the sender and receiver of the encrypted sensitive information. The public key is also called asymmetric cryptography.
The following are some of the important differences between Private Key and Public Key.
Java Read Public Key Generate Private Keys
| Sr. No. | Key | Private Key | Public Key |
|---|---|---|---|
| 1 | Algorithm | Private Key is used to both encrypt and decrypt the data and is shared between the sender and receiver of encrypted data. | The public key is only used to encrypt data and to decrypt the data, the private key is used and is shared. |
| 2 | Performance | The private key mechanism is faster. | The public key mechanism is slower. |
| 3 | Secret | The private key is kept secret and not public to anyone apart from the sender and receiver. | The public key is free to use and the private key is kept secret only. |
| 4 | Type | The private key mechanism is called symmetric being a single key between two parties. | The public key mechanism is called asymmetric being two keys for different purposes. |
| 5 | Sharing | The private key is to be shared between two parties. | The public key can be used by anyone but the private key is to be shared between two parties only. |
| 6 | Targets | Performance testing checks the reliability, scalability, and speed of the system. | Load testing checks the sustainability of the system. |